Network Segmentation: Difference between revisions
From GCA ACT
Jump to navigationJump to search
No edit summary |
No edit summary |
||
| Line 2: | Line 2: | ||
|- | |- | ||
| colspan="4" | | | colspan="4" | | ||
<big>'''Introduction'''</big><br> | [[File:ACT_Network_Segmentation_Icon.svg|frameless|40px|link=Network Segmentation]] <big>'''Introduction'''</big><br> | ||
Network segmentation is a crucial strategy in the field of cybersecurity. It involves dividing a network into smaller, isolated segments or subnetworks to enhance security and limit the potential impact of a security breach. This technique is employed by both individuals and organizations to protect sensitive data, systems, and resources from unauthorized access and cyber threats. | Network segmentation is a crucial strategy in the field of cybersecurity. It involves dividing a network into smaller, isolated segments or subnetworks to enhance security and limit the potential impact of a security breach. This technique is employed by both individuals and organizations to protect sensitive data, systems, and resources from unauthorized access and cyber threats. | ||
|- | |- | ||
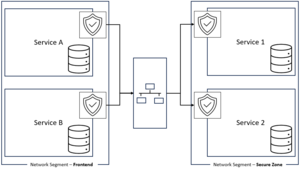
| colspan="2" | <big>'''Organizations'''</big><br> | | colspan="2" | <big>'''Organizations'''</big><br> | ||
Network segmentation is a vital cybersecurity strategy for organizations of all sizes in today's digital landscape. Each isolated segment can be equipped with its own security measures and access controls. This allows organizations mitigate the ever-evolving threats posed by cyberattacks, safeguard sensitive data, and maintain business continuity. | Network segmentation is a vital cybersecurity strategy for organizations of all sizes in today's digital landscape. Each isolated segment can be equipped with its own security measures and access controls. This allows organizations mitigate the ever-evolving threats posed by cyberattacks, safeguard sensitive data, and maintain business continuity. | ||
[[File:network_segmentation_organization.png|frameless|left|Traditional Network Segmentation]] | |||
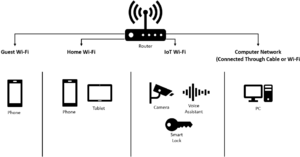
| colspan="2" | <big>'''Individuals'''</big><br> | | colspan="2" | <big>'''Individuals'''</big><br> | ||
Network segmentation is not just for large organizations; individuals can also use this cybersecurity strategy to enhance their online security and privacy. It involves dividing your home network into isolated segments to limit potential security risks and control access to your devices and data. | Network segmentation is not just for large organizations; individuals can also use this cybersecurity strategy to enhance their online security and privacy. It involves dividing your home network into isolated segments to limit potential security risks and control access to your devices and data. | ||
[[File:network_segmentation_individuals.png|frameless|left|Home Network Segmentation]] | |||
|- | |- | ||
| <big>'''Benefits'''</big><br> | | <big>'''Benefits'''</big><br> | ||