Network Segmentation: Difference between revisions
From GCA ACT
Jump to navigationJump to search
No edit summary |
No edit summary |
||
| (2 intermediate revisions by one other user not shown) | |||
| Line 5: | Line 5: | ||
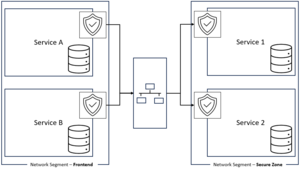
Network segmentation is a crucial strategy in the field of cybersecurity. It involves dividing a network into smaller, isolated segments or subnetworks to enhance security and limit the potential impact of a security breach. This technique is employed by both individuals and organizations to protect sensitive data, systems, and resources from unauthorized access and cyber threats. | Network segmentation is a crucial strategy in the field of cybersecurity. It involves dividing a network into smaller, isolated segments or subnetworks to enhance security and limit the potential impact of a security breach. This technique is employed by both individuals and organizations to protect sensitive data, systems, and resources from unauthorized access and cyber threats. | ||
| colspan="2" valign="top"| | | colspan="2" valign="top"| | ||
[[File:Elephants.png|frameless|100px|right|link= | [[File:Elephants.png|frameless|100px|right|link=Advanced_Security]] | ||
{| role="presentation" class="wikitable mw-collapsible mw-collapsed" | |||
| <strong>Cybersecurity Tools</strong> | |||
|- | |||
| | |||
{{#categorytree:Network Devices|mode=pages|all}} | |||
|} | |||
|- | |- | ||
| colspan="2" valign="top" | <big>'''Organizations'''</big><br> | | colspan="2" valign="top" | <big>'''Organizations'''</big><br> | ||
| Line 53: | Line 58: | ||
|- | |- | ||
| | | | ||
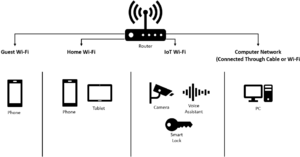
[[File:enhanced_privacy_icon | [[File:enhanced_privacy_icon.png|frameless|15px]] '''Enhanced Privacy''': Network segmentation provides better control over who can access your devices and data. Your personal devices and sensitive information are less exposed to potential threats.<br> | ||
.png|frameless|15px]] '''Enhanced Privacy''': Network segmentation provides better control over who can access your devices and data. Your personal devices and sensitive information are less exposed to potential threats.<br> | |||
[[File:improved_security_icon.png|frameless|15px]] '''Improved Security''': If one segment is compromised, the rest of your network remains protected. This containment can prevent the spread of malware and unauthorized access.<br> | [[File:improved_security_icon.png|frameless|15px]] '''Improved Security''': If one segment is compromised, the rest of your network remains protected. This containment can prevent the spread of malware and unauthorized access.<br> | ||
[[File:network_management_icon.png|frameless|15px]] '''Efficient Network Management''': Separating devices into segments makes it easier to manage your network and troubleshoot issues. You can identify and address problems in specific segments without affecting the entire network.<br> | [[File:network_management_icon.png|frameless|15px]] '''Efficient Network Management''': Separating devices into segments makes it easier to manage your network and troubleshoot issues. You can identify and address problems in specific segments without affecting the entire network.<br> | ||