Network Segmentation: Difference between revisions
From GCA ACT
Jump to navigationJump to search
No edit summary |
|||
| (17 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
= Network Segmentation | {| class="wikitable" | ||
|- | |||
| colspan="2" valign="top"| | |||
[[File:ACT_Network_Segmentation_Icon.svg|frameless|40px|link=Network Segmentation]] <big>'''Introduction'''</big><br> | |||
Network segmentation is a crucial strategy in the field of cybersecurity. It involves dividing a network into smaller, isolated segments or subnetworks to enhance security and limit the potential impact of a security breach. This technique is employed by both individuals and organizations to protect sensitive data, systems, and resources from unauthorized access and cyber threats. | Network segmentation is a crucial strategy in the field of cybersecurity. It involves dividing a network into smaller, isolated segments or subnetworks to enhance security and limit the potential impact of a security breach. This technique is employed by both individuals and organizations to protect sensitive data, systems, and resources from unauthorized access and cyber threats. | ||
= | | colspan="2" valign="top"| | ||
[[File:Elephants.png|frameless|100px|right|link=Advanced_Security]] | |||
[[File: | {| role="presentation" class="wikitable mw-collapsible mw-collapsed" | ||
| <strong>Cybersecurity Tools</strong> | |||
|- | |||
| | |||
{{#categorytree:Network Devices|mode=pages|all}} | |||
|} | |||
|- | |||
| colspan="2" valign="top" | <big>'''Organizations'''</big><br> | |||
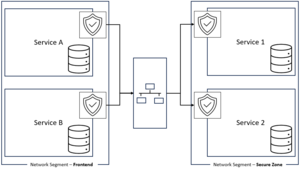
Network segmentation is a vital cybersecurity strategy for organizations of all sizes in today's digital landscape. Each isolated segment can be equipped with its own security measures and access controls. This allows organizations mitigate the ever-evolving threats posed by cyberattacks, safeguard sensitive data, and maintain business continuity. | Network segmentation is a vital cybersecurity strategy for organizations of all sizes in today's digital landscape. Each isolated segment can be equipped with its own security measures and access controls. This allows organizations mitigate the ever-evolving threats posed by cyberattacks, safeguard sensitive data, and maintain business continuity. | ||
[[File:network_segmentation_organization.png|frameless|left|Traditional Network Segmentation]] | |||
| colspan="2" valign="top" | <big>'''Individuals'''</big><br> | |||
== | |||
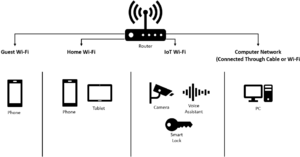
Network segmentation is not just for large organizations; individuals can also use this cybersecurity strategy to enhance their online security and privacy. It involves dividing your home network into isolated segments to limit potential security risks and control access to your devices and data. | Network segmentation is not just for large organizations; individuals can also use this cybersecurity strategy to enhance their online security and privacy. It involves dividing your home network into isolated segments to limit potential security risks and control access to your devices and data. | ||
[[File:network_segmentation_individuals.png|frameless|left|Home Network Segmentation]] | |||
|- | |||
| valign="top" | | |||
{| role="presentation" class="wikitable mw-collapsible mw-collapsed" | |||
| <strong>Organizational Benefits</strong> | |||
|- | |||
| | |||
[[File:security_icon.png|frameless|15px]] '''Enhanced Security''': One of the primary benefits of network segmentation is improved security. By dividing a network into smaller segments, organizations can create barriers that prevent unauthorized access between segments. This makes it significantly more challenging for cybercriminals to move laterally within a network if they manage to breach one segment.<br> | |||
[[File:recude_icon.jpg|frameless|15px]] '''Reduced Attack Surface''': Network segmentation reduces the attack surface, which is the total area vulnerable to cyberattacks. By isolating different parts of the network, the potential attack vectors are minimized, making it harder for attackers to compromise critical systems.<br> | |||
[[File:isolation_icon.png|frameless|15px]] '''Isolation of Sensitive Data''': Organizations can isolate sensitive data, such as financial records or customer information, in dedicated segments. This ensures that even if one segment is breached, the sensitive data remains protected in another.<br> | |||
[[File:regulation_icon.png|frameless|15px]] '''Compliance and Regulation''': Many industry regulations and compliance standards require organizations to implement network segmentation as a security measure. Compliance with these standards is crucial for avoiding fines and legal repercussions.<br> | |||
[[File:optimization_icon.png|frameless|15px]] '''Resource Optimization''': Network segmentation allows for better resource allocation. For example, bandwidth-intensive applications can be isolated to specific segments to ensure that they do not impact the performance of other network segments. | |||
|} | |||
| valign="top" | | |||
{| role="presentation" class="wikitable mw-collapsible mw-collapsed" | |||
| <strong>Organizational Impact</strong> | |||
|- | |||
| | |||
[[File:incident_response_icon.png|frameless|15px]] '''Improved Incident Response''': In the event of a security incident, network segmentation helps contain the breach. This containment limits the damage caused and allows security teams to respond more effectively without affecting the entire network.<br> | |||
[[File:data_exposure_icon.jpg|frameless|15px]] '''Minimized Data Exposure''': If a breach occurs, the segmented structure minimizes the amount of data exposed, reducing the potential harm to an organization's reputation and financial well-being.<br> | |||
[[File:access_control_icon.png|frameless|15px]] '''Better Access Control''': Network segmentation enables granular control over who can access specific segments. This ensures that only authorized personnel have access to critical systems and resources.<br> | |||
[[File:adaptability_icon.png|frameless|15px]] '''Adaptability''': Organizations can adapt network segmentation to their specific needs. Segments can be created or modified as the organization's requirements evolve, allowing for a flexible and scalable security strategy.<br> | |||
[[File:reduce_risk_icon.png|frameless|15px]] '''Reduced Risk''': By proactively implementing network segmentation, organizations can significantly reduce the risk of a successful cyberattack. This helps protect sensitive information, maintain business continuity, and safeguard reputation. | |||
|} | |||
| valign="top" | | |||
{| role="presentation" class="wikitable mw-collapsible mw-collapsed" | |||
| <strong>Individual Benefits</strong> | |||
|- | |||
| | |||
[[File:devoce_isolation_icon.png|frameless|15px]] '''Device Isolation''': By segmenting your network, you can isolate different types of devices. For example, you can place your smart home devices (e.g., smart thermostats, cameras) in a separate segment from your personal computers and smartphones. This prevents a security breach on one type of device from compromising your entire network.<br> | |||
[[File:guest_icon.png|frameless|15px]] '''Guest Network''': Set up a separate guest network for visitors. This network can have limited access and be isolated from your main network, preventing guests from accidentally or intentionally accessing your sensitive data.<br> | |||
[[File:iot_icon.png|frameless|15px]] '''IoT Security''': With the proliferation of Internet of Things (IoT) devices, network segmentation is crucial. Isolating your IoT devices can protect your main network from potential vulnerabilities in these devices.<br> | |||
[[File:parental_control_icon.png|frameless|15px]] '''Parental Control'''*: If you have children, network segmentation can help implement parental control measures. You can create a separate network segment for their devices and apply content filtering or time restrictions.<br> | |||
[[File:security_testing_icon.png|frameless|15px]] '''Security Testing''': Network segmentation allows you to test security measures on a limited scale without risking your entire network. You can experiment with different security configurations on one segment to assess their effectiveness. | |||
|} | |||
| valign="top" | | |||
{| role="presentation" class="wikitable mw-collapsible mw-collapsed" | |||
| <strong>Individual Impact</strong> | |||
|- | |||
| | |||
[[File:enhanced_privacy_icon.png|frameless|15px]] '''Enhanced Privacy''': Network segmentation provides better control over who can access your devices and data. Your personal devices and sensitive information are less exposed to potential threats.<br> | |||
[[File:improved_security_icon.png|frameless|15px]] '''Improved Security''': If one segment is compromised, the rest of your network remains protected. This containment can prevent the spread of malware and unauthorized access.<br> | |||
[[File:network_management_icon.png|frameless|15px]] '''Efficient Network Management''': Separating devices into segments makes it easier to manage your network and troubleshoot issues. You can identify and address problems in specific segments without affecting the entire network.<br> | |||
[[File:peace_of_mind_icon.png|frameless|15px]] '''Peace of Mind''': Knowing that your devices and data are compartmentalized can give you peace of mind, especially in an era of increasing cyber threats.<br> | |||
[[File:customization_icon.png|frameless|15px]] '''Customization''': Network segmentation allows you to customize security settings for each segment according to your specific needs and preferences.<br> | |||
Implementing network segmentation at home may require some technical knowledge, but it can significantly improve your cybersecurity posture. It's an effective way to protect your devices, personal information, and privacy in an interconnected world. | |||
|} | |||
|} | |||